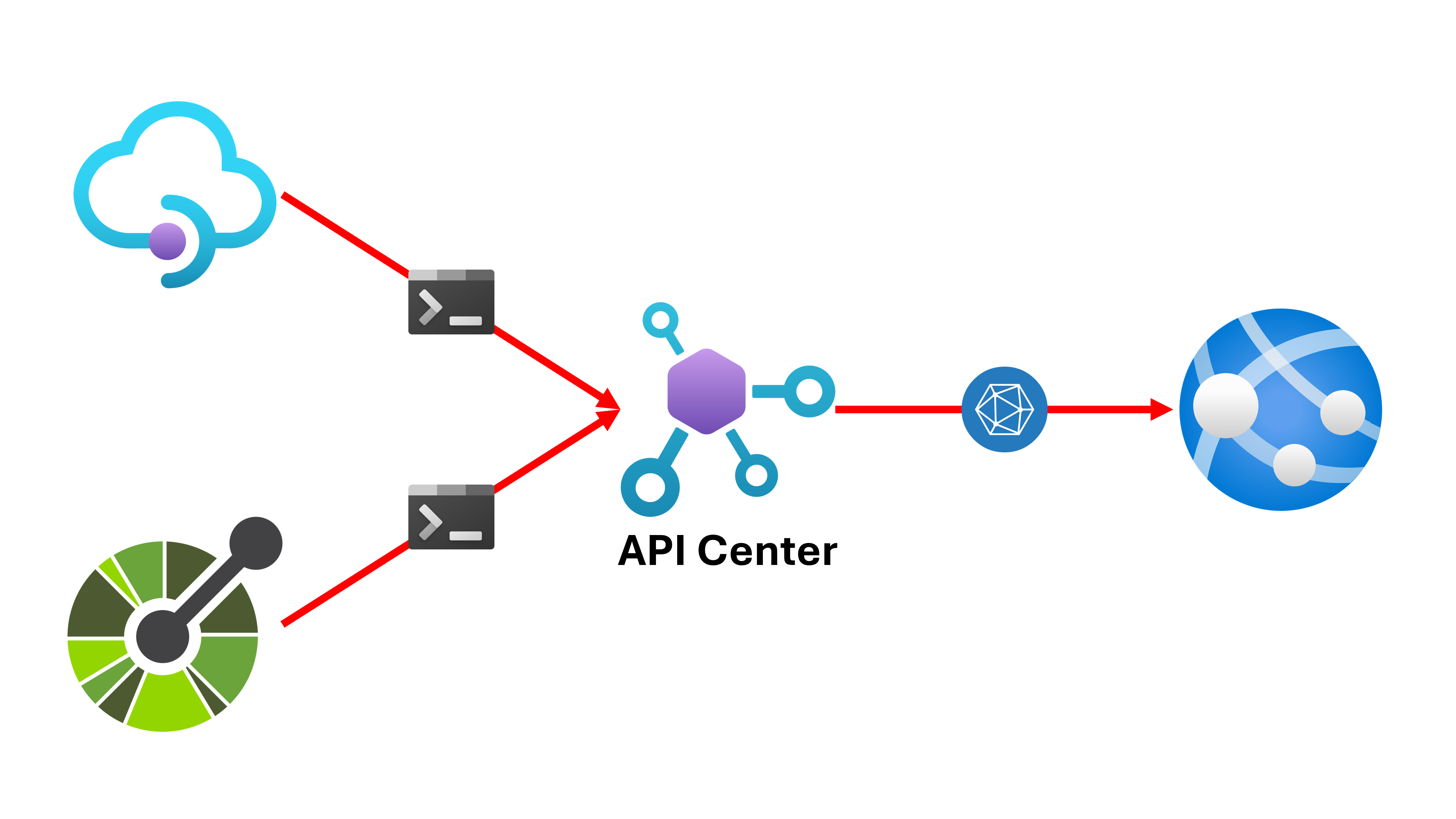
Giving Granular Controls to Azure EasyAuth
by Justin Yoo in Azure · 6 min read
When working with web applications, implementing authentication and authorization is crucial for security. Traditionally, there have been various ways from simple username/password inputs to